Read time: 4 minutes 26 seconds

I’ve been thinking a lot recently about ‘building-in-public’.
→ Why it’s such a powerful idea.
→ How the best companies are doing it.
→ How Strategy Breakdowns can do more of it. (hint)
Today’s piece is a riff in the same key, unpacking a transparency-led strategy that turned Cloudflare into one of the internet’s most-loved companies.
Enjoy.
— Tom

Stop guessing. Start winning.
Ever wondered exactly what makes your competitors’ marketing outperform yours?
Try Ahrefs - the marketing intelligence tool that reveals their every move.
Data-backed insights. Actionable recommendations. Free version available.
My Playbook to Discover Hidden Opportunities
StrategyHub gives you the exact system I used at Atlassian to make high-impact strategic decisions using free online data.
Become your company's go-to 'insights person' by spotting patterns and opportunities that others miss.
Thank you for supporting our sponsors, who keep this newsletter free.



Chess Move
The what: A TLDR explanation of the strategy
Imagine you have 2 companies wanting to increase customer trust:
Company 1 decides that whenever they make a mistake or experience a service breach/outage/vulnerability, they keep quiet.
(“The last thing we want is for our customers to find out! Better to keep a clean slate with no issues visible to the public.”)
Company 2 takes the opposite approach - outwardly committing to total transparency: publicly sharing mistakes, publishing deep technical analysis of any breach/outage/vulnerability, and maintaining an extensive monitoring and alerts platform to share real-time information with customers.
Which company builds more trust?
Counterintuitively, Company 2’s strategy creates a tangible moat, due to something I call “The Trust <> Transparency Paradox”.
If you aren’t transparent with ‘negative’ news, customers have no way to tell if:
You have nothing to report because you’re nailing everything, or
You have nothing to report because you’re hiding something
If you publicly commit to total transparency, customers trust that:
If something ‘negative’ happens, they’ll hear about it
If nothing is reported, then nothing ‘negative’ happened
The more perfect you appear transparent you are, the more trusted you become.
Cloudflare, one of the world’s largest web app security and performance platforms, is Company 2.
By betting the house on the Trust <> Transparency Paradox, they’ve grown to over 40 million customers, across a global network of 310+ data centres, serving 22% of all internet traffic.
Here’s how they did it.
💡
Strategy Playbook: Transform ‘negative news’ from a liability into an asset.


Breakdown
The how: The strategic playbook boiled down to 3x key takeaways
1. Incidents are opportunities
The typical response to security incidents is to minimise disclosure, control the narrative, and release sparse details (when absolutely necessary).
Cloudflare does the inverse: rapidly publish exhaustive incident post-mortems that read more like technical case studies than PR statements.
Take their 2nd July 2019 outage, which affected platforms like Discord, Shopify, and Zendesk.
Cloudflare instantly published a short placeholder blog to notify the public of the incident, promising a full post-mortem.

Within 24 hours, they published a 2,800-word analysis of the incident with a striking level of detail.

Alerts received on the CTO’s watch

Minute-by-minute technical data

Internal process maps for software release

Build log of the breaking change

Overview of precisely what went wrong

Outline of systemic changes they’ve made since to prevent similar issues
They didn't just admit a mistake happened, they walked readers through the entire chain of events, including how their own deployment processes failed.
Notably, CTO John Graham-Cumming personally signed off on the post-mortem, directly associating leadership with the transparent explanation.
This approach turned a damaging incident into evidence of their technical competence and trustworthiness.
The ‘Trust <> Transparency Paradox’ creates a powerful dynamic: the more open they are about their failures, the more customers trust their competence to handle future challenges.
2. Industrialised transparency
It’s one thing to post blog updates about issues.
It’s another thing entirely to build an automated, public-facing monitoring and alerts system that eliminates any possibility of keeping customers in the dark.
Cloudflare’s System Status page isn't just a simple "green/red" indicator - it's a granular, real-time dashboard that shares:

Current status of hundreds of specific sites and services

Operational standing of hundreds of data centres worldwide

Minute-by-minute updates during active incidents
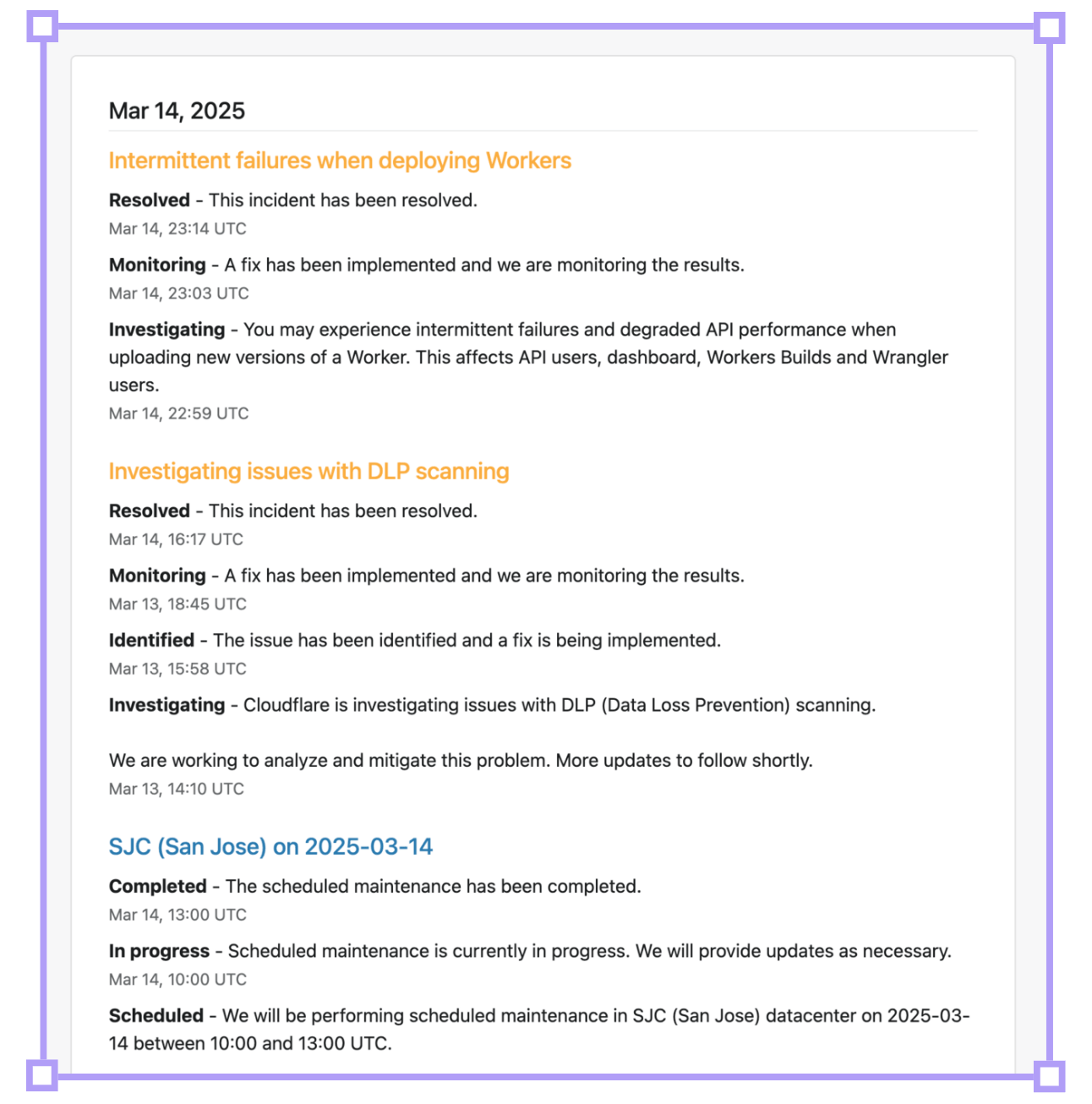
Detailed incident histories going back years
All data on the public System Status page is also available programatically via the Cloudflare Status API, email, PagerDuty, and webhooks, allowing customers to not only stay notified, but also incorporate Cloudflare notifications into their own internal systems and customer-facing products.


Then there’s the Network Analytics platform, which gives Enterprise customers near real-time visibility into:
Network performance across global infrastructure
DDoS attack detection and mitigation efforts
Traffic patterns at the packet and bit level
16 weeks of historical performance data

Side-note: I can instantly tell this diagram was made in Excalidraw because of the scribbly fonts and arrows. Just like you can recognise a screenshot of a Notion workspace, or a Stripe MRR dashboard. Visual distinctiveness as a growth lever.
Cloudflare’s systematised transparency stands in stark contrast to companies that wait hours to acknowledge issues or use fuzzy language like "we're experiencing elevated error rates in some regions."
By engineering trust into their infrastructure, Cloudflare made transparency a technical inevitability (not just a policy).
3. Show your work
Cloudflare could have followed the established industry pattern of security vendors looking to differentiate their product: make vague claims about ‘advanced protection’ without revealing how it works.
Instead, they openly publish their research:
Detailed explanations of their CAPTCHA alternatives and bot detection techniques
The reference architecture behind their Zero Trust network access solution
Novel DDoS mitigation strategies that reveal their defensive playbook
Implementation details of cryptographic systems like SSL/TLS
This open approach benefits Cloudflare in multiple ways:
It positions them as thought leaders. By publishing detailed technical content, they demonstrate intellectual leadership before customers even try their products.
It creates powerful content marketing. Their blog serves as both a knowledge base and a lead generation tool - drawing in technical decision-makers without appearing promotional.
It helps recruit top talent. Security researchers and engineers are drawn to companies where they can publish their work and contribute to advancing the field.
Perhaps most interestingly, Cloudflare's approach creates an unusual form of competitive moat:
By openly publishing their techniques, they appear confident and ahead of both competitors and attackers.
They effectively signal that "we're moving so quickly that even if everyone knows what we're doing, they'll struggle to catch up."
Their strategy creates a virtuous cycle:
→ Detailed post-mortems and technical content attract security-conscious engineers
→ Top talent produces innovative research and improved security practices
→ Better security and transparency build customer trust
→ Trust leads to more adoption
→ More customers provide larger datasets for security improvements
→ Enhanced solutions generate more material for transparent content

Heuristic: Do enough things that build trust to justify building a ‘Trust Hub’
Cloudflare proved that transparency paradoxically creates multiple compounding advantages in an industry built upon secrecy.

Rabbit Hole
The where: 3x high-signal resources to learn more
[8 minute read]
I’m a sucker for a good business strategy → game strategy analogy.
This one works on so many levels.
Easily my favourite thing I read when researching this article.
[4 minute read]
Director of Product Content Kim Jeske unpacks Cloudflare’s unique content philosophy: treating content as a dynamic product.
Product development mindset. Shipping fast. User-focussed design. Built-in feedback loops. Open-source platform.
Valuable read for the budding content strategists out there.

[10 minute read]
Given the vast amount of information transiting their global network, every year Cloudflare gets hundreds of data requests from governments, courts, etc:
Subpoenas
WHOIS Data Disclosures
Search warrants
Wiretaps
National security investigations
The ‘Transparency Report’ is a semi-annual analysis published to ensure these requests are counted, documented, and known to the public.
Ngl the volume of requests they get each year is pretty wild.
That’s all for today’s breakdown - hope you enjoyed!
Don’t forget to check out our wonderful sponsors ahrefs and ReadyLetter.
— Tom
P.S. Want to see the radically transparent story behind Strategy Breakdowns? I’ve got something for you here.


Whenever you're ready, there are 3 ways we can help you:
Our flagship course on how to use free internet data to make better strategic decisions. Contains 5 years of strategy expertise, proven methods, and actionable tactics to accelerate your career with modern-day strategy skills.
We have a growing audience of 70,000+ strategists from top companies like Google, Meta, Atlassian, Stripe, and Netflix. Apply to feature your business in front of Strategy Breakdowns readers.
One of the most common questions we get asked is: “What tools do you use to run Strategy Breakdowns?” So, we’ve open-sourced our tech stack to give you an inside-look at exactly what tools we’re using to power each corner of this operation.